My team and I spend our 9 to 5 working on the SAP ERP Connector for Power Apps/Automate. A key focus of our work is ensuring secure, encrypted transit when connecting to SAP, particularly for production systems. This vital security measure is designed to protect your data from interception or exposure during transit and to guard against man-in-the-middle attacks.
While securing connections to SAP, we shift from the typical TLS (Transport Layer Security) to public key encryption, known as Secure Network Communications (SNC). This approach mirrors the standard practice of verifying website security like checking for the lock icon in a browser's URL bar but with a focus tailored for SAP's unique requirements.
For more insights, updates, and discussions on this and related topics, feel free to connect with me on X (formerly Twitter) at @Ryanb58. Now, let's examine a data flow diagram from Power App/Flow to SAP:
Notice how, in the diagram, the connection between the On-Premises Data Gateway (OPDG) and SAP is unencrypted. Although this might not pose a significant risk if both systems are securely isolated within your local network, adopting SNC offers a straightforward solution to enhance your data's security. SNC ensures that your sensitive information remains out of reach from unauthorized access and simplifies the technical process.
As we delve into the technical steps, feel free to adapt parts of this tutorial as needed. Remember, not all steps may apply to every scenario, so some improvisation might be necessary.
Setting Up SNC between SAP and OPDG
Pre-Requisite
- S-User Account on SAP's website(Helpful when resolving error messages and downloading required resources)
- Windows Machine with the latest OPDG Installed
- SAP Instance
- Ability to Restart
- Administrator Account
- SAP GUI with login
- OpenSSL
- If you have
Git for Windowsinstalled, then you can access theopensslcommand by opening upGit Bash. - If you are without, do not fear, you can use winget to install a distribution of it built by FireDaemon.
winget install --id FireDaemon.OpenSSL
- If you have
SAP Common Crypto
SAP Common Crypto is a distribution from SAP that allows the OPDG to talk to SAP in an encrypted way. It will come as a .SAR file type, so we will need it and a way to extract the data from it.
Download SAPCAR
- Go to the SAP Software Center.
- Type
SAPCARinto theSearch for Software Downloadssearch box. - Click on the top result(non archived).
- From there, select the latest version. At the time of this writing I selected
SAPCAR 7.53. -
Select the operating system type in the dropdown located above the search results.
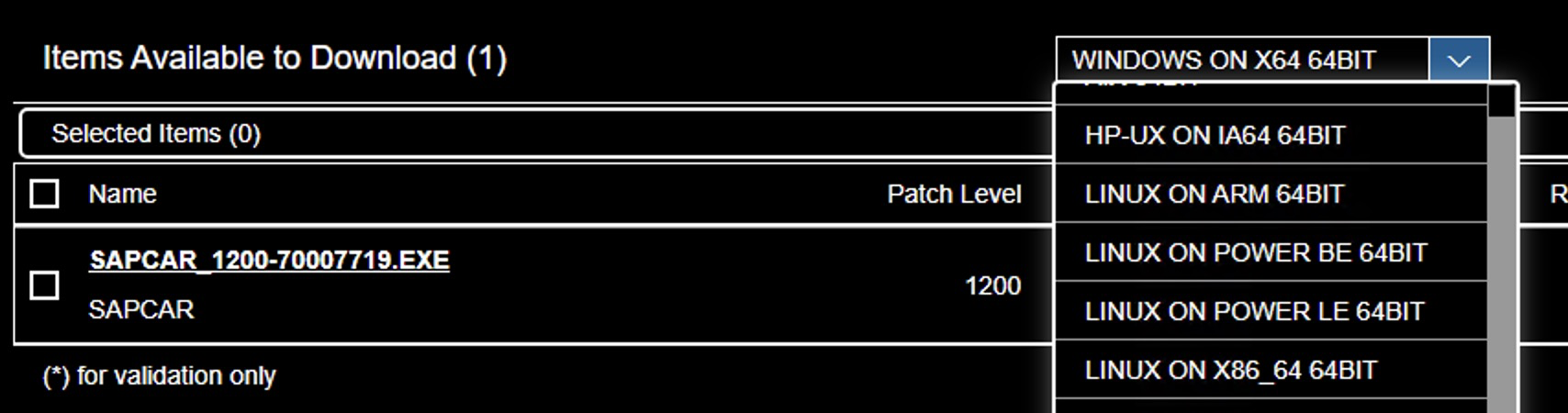
-
Click on the result to download the .EXE file. I placed mine in
C:\sap\SAR
Download SAP Common Crypto
- Go back to the SAP Software Center.
- Type
COMMONCRYPTOLIBinto theSearch for Software Downloadssearch box. - Select the
COMMONCRYPTOLIB 8result. - Select the operating system type in the dropdown located above the search results.
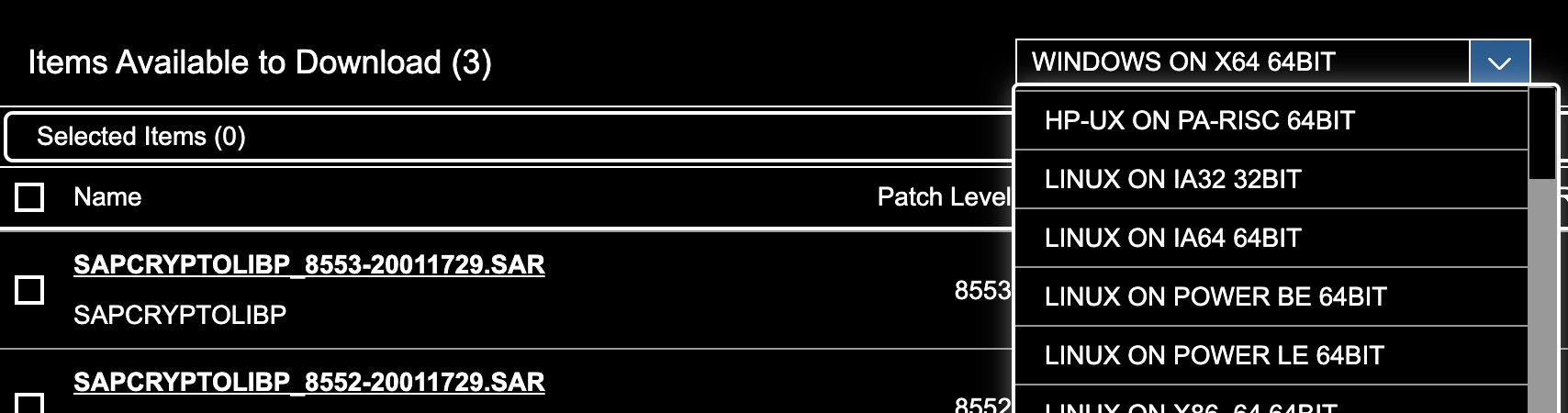
- Click on the title of the listing with the most recent
Release Dateto download the .SAR file.
Extract SAP Common Crypto
- Open a PowerShell window to
C:\sap\SAR. - Extract SAP Common Crypto using the command below.
.\SAPCAR_1200-70007719.EXE -xvf .\SAPCRYPTOLIBP_8553-20011729.SAR -R .\..\libs\sapcryptolib - This will extract the files to
C:\sap\libs\sapcryptolib. - You should see
sapgenpse.exein the folder. This is an important program we will use later on.
Setting up SECUDIR environment variable on the OPDG
We will start by creating this named folder. The name in itself does not matter, but for this tutorial we will use sapsecudir and we will put it in the root directory.
C:\> mkdir sapsecudir
C:\> cd .\sapsecudirDefine an environment variable called SECUDIR and point it at that directory.
First we backup our existing PATH environment variable into a file.
C:\sapsecudir> $env:path >> ("env-PATH_" + (Get-Date -Format "yyyy-MM-dd_HH-mm-ss") + ".out")And permanently add SECUDIR to our machine. This variable will persist between restarts.
[Environment]::SetEnvironmentVariable("SECUDIR", "C:\sapsecudir", "Machine") # Sets the variable permentaly on the system.
$env:SECUDIR = "C:\sapsecudir" # Updates the current powershell session as there currently does not exist a function to reload.Then restart your On-Premises Data Gateway for the changes to take effect.
Generating Certificates
Some of you might already have a PKI setup. In this tutorial, I do not have one, so I will create one on the fly that can be expanded to X.509 user authentication later on.
Below is a visual to help with understanding of what certificate will do what and how it can be expanded to issue user certs in the future. In this tutorial we will focus on implementing the blue boxes.
This section is not recommended for production systems, however is a good way to get a demo up and running quickly.
Now we are ready to create the folder structure for our certificates. Navigate to a secure place on your disk that'll you'll keep around, as we will be generating sensitive data here.
mkdir rootCA sncCert intermediateUsersCert userCerts
echo 1000 > serial
touch index.txtGenerate a Root CA(Certificate Authority)
openssl genpkey -algorithm RSA -out rootCA/ca.key.pem -pkeyopt rsa_keygen_bits:2048
openssl req -x509 -new -key rootCA/ca.key.pem -days 7305 -sha256 -extensions v3_ca -out rootCA/ca.cert.pem -subj "/O=Contoso/CN=Root CA"Generate the SNC certificate.
openssl genrsa -out sncCert/snc.key.pem 2048
openssl req -key sncCert/snc.key.pem -new -sha256 -out sncCert/snc.csr.pem -subj "/O=Contoso/CN=SNC"Sign the SNC cert with the RootCA cert.
openssl x509 -req -in sncCert/snc.csr.pem -days 3650 -CA rootCA/ca.cert.pem -CAkey rootCA/ca.key.pem -CAcreateserial -out sncCert/snc.cert.pemVerify the SNC certificate.
openssl x509 -in sncCert\snc.cert.pem -textPlacing the SNC Certificate into a PSE for the OPDG
Add the SNC cert to an SSL container p12.
openssl pkcs12 -export -out snc.p12 -inkey sncCert\snc.key.pem -in sncCert\snc.cert.pem -certfile rootCA\ca.cert.pemCreate the .PSE!
C:\sap\libs\sapcryptolib\sapgenpse.exe import_p12 -p SAPSNCSKERB.pse C:\Users\tbrazelton\Documents\sap-kerb\04\snc.p12Configuring SAP for SNC
- Log into the SAP GUI.
- Go to t-code
RZ10. - Ensure the following properties are set.
- Talk to your SAP basis About these changes.
- Change
snc/identity/asONLY if needed. (usually this is not needed). Butsnc/accept_insecure_cpic: 1 snc/accept_insecure_gui: 1 snc/accept_insecure_rfc: 1 snc/enable: 1 snc/extid_login_diag: 1 snc/extid_login_rfc: 1 snc/gssapi_lib: $(SAPCRYPTOLIB) snc/identity/as: p:CN=ID3, O=Contoso snc/permit_insecure_start: 1 snc/data_protection/max: 3
- Save the profile parameters and restart your SAP instance.
SAP Box Certificate Setup Instructions
Adding Our OPDG's SNC Public Cert to SAP
- Log into SAP GUI
- Go to t-code
STRUST - If the
SNC SAPCryptolibhas a redXnext to it, we will need to right click on it and selectCreate. This will create an PSE on the SAP system to store certificates. - Double click the
SNC SAPCryptolibfolder. Then double click on the Subject of your Own Certificate in the top right panel. - Select the
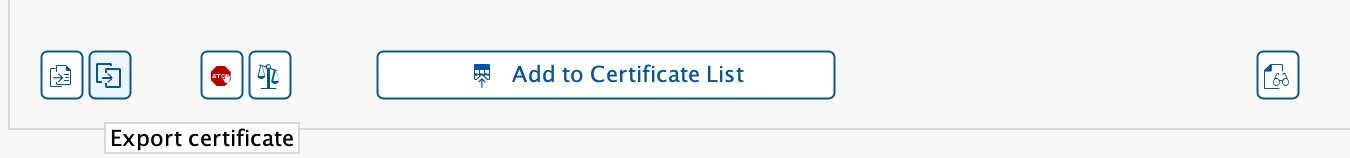
Import Certificatebutton at the bottom of the page and select yoursncCert\snc.cert.pemfile. - Click the
Add to Certificate Listbutton.- If the
Add to Certificate Listbutton is grayed out, make sure you select theChangebutton as pictured below.
- If the

Adding Our SAP Boxes SNC Public Cert to OPDG
- Similar to the steps above, Log into the SAP GUI
- Go to t-code
STRUST - Double click the
SNC SAPCryptolibfolder. Then double click on the Subject of your Own Certificate in the top right panel. - Scroll down the page and export the public cert.
- Move the public cert to your OPDG box(I placed mine in C:\sap\contoso-public-key.crt).
- Use the following command to import it into your OPDG's PSE.
C:\sap\libs\sapcryptolib\sapgenpse.exe maintain_pk -p SAPSNCSKERB.pse -v -a C:\sap\contoso-public-key.crt - Trust has now been established between your SAP box and the OPDG box!
Testing Communication
Create a new instant flow in Power Automate. Add an SAP ERP Call Function action to the designer and modify your SAP System string to include the following substituting my system info with your own.
You can find the SncMyName of your system under t-code STRUST > SNC SAPCryptolib (Noted as the subject of your own certificate).
{
"AppServerHost": "xxx",
"Client": "xx",
"SystemNumber": "xx",
"LogonType": "ApplicationServer",
"SncMyName": "p:CN=SNC, O=Contoso",
"SncLibraryPath": "C:\\sap\\libs\\sapcryptolib\\sapcrypto.dll",
"SncPartnerName": "p:CN=ID3, O=Contoso",
"SncQop": "Default",
"UseSnc": "true",
"SncSso": "Off"
}Then test it out with the "STFC_CONNECTION" RFC function.
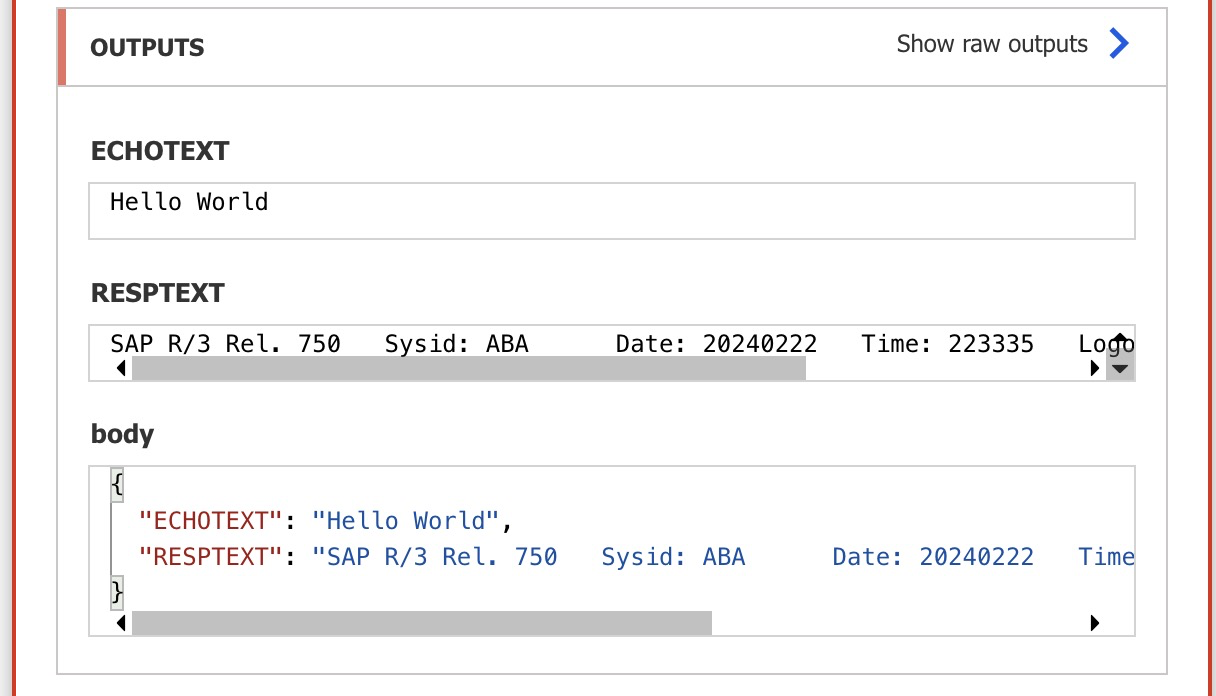
Enjoy your fully encrypted connection!
If you have any questions, improvements, or general comments, please feel free to ping me on X(formally Twitter).